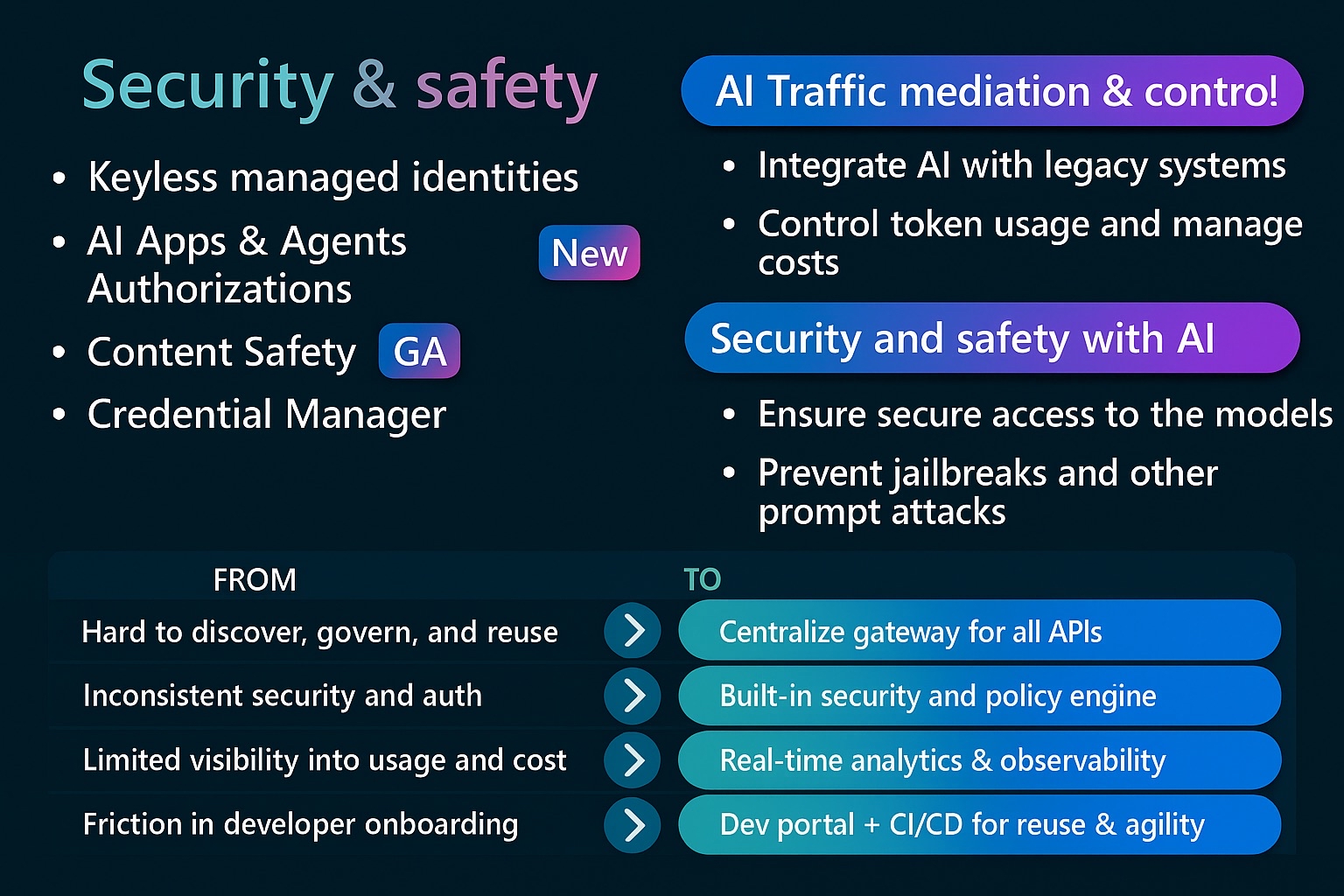
Integrate 2025: What You Really Need to Explore Now
Contica’s CTO and Microsoft Azure MVP, Ahmed Bayoumy, shares his reflections from Integrate 2025. AI agents aren’t the future—they’re the new normal. This is your essential checklist for what to explore now to stay ahead in an increasingly intelligent integration landscape.
Integrate 2025: Your Essential Exploration Checklist
Yes, everything is AI and AI agents now. And yes, we can’t ignore it anymore.
The Reality Check
After Integrate 2025, one thing became crystal clear: There’s no way back from this.
I know, I know, another “AI will change everything” article. But hear me out. This isn’t about hype anymore. Microsoft just showed us a world where AI agents are handling loan approvals, fixing production issues at 3 AM, and making business decisions that used to require human judgment.
The most surprising part? These aren’t prototypes or far-future concepts. They’re shipping today. Whether you’re ready or not, the AI agent revolution is already here. The question isn’t “if” you should explore this technology, but “what exactly” you need to explore to stay relevant.
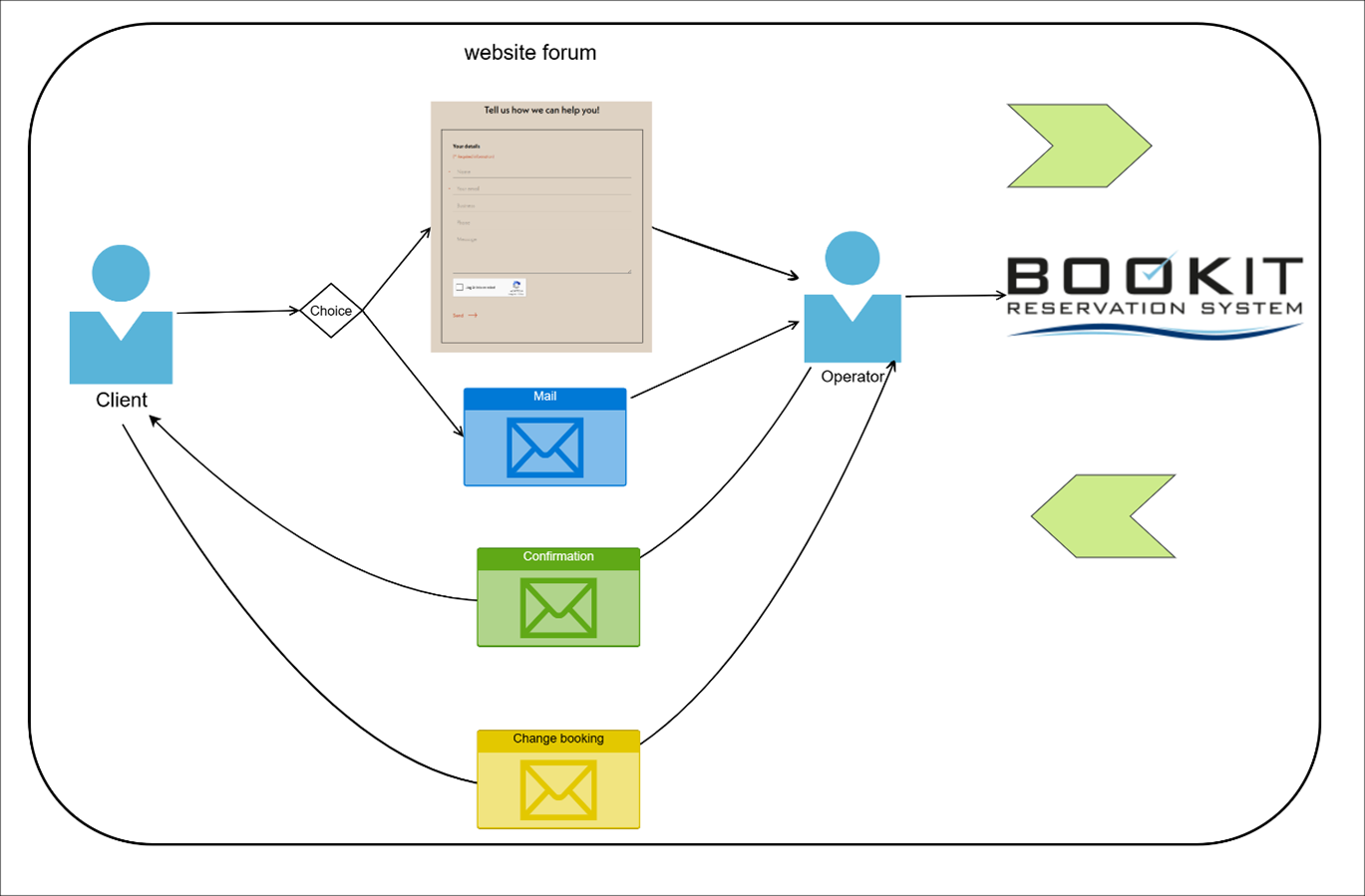
Looking at below, I can see that a lot of businesses are running a few steps behind, and we need to reshape our thinking to simply keep up. Instead of rigid, rule-based integrations, we’re moving toward intelligent workflows that can reason through complex scenarios.
We in phase 8 → AI Agents represent the next evolutionary step
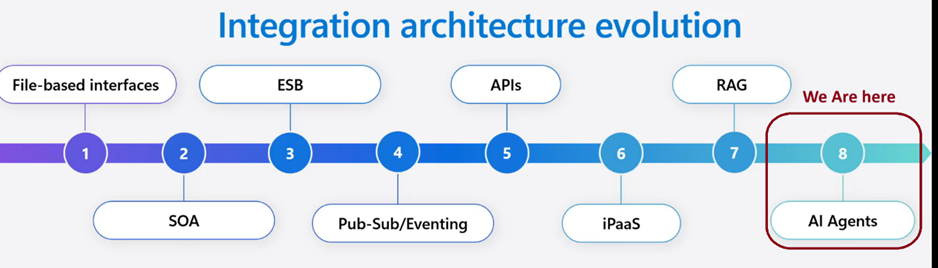
In this article, I thought of sharing my plan navigating this new reality your essential exploration checklist for the post-Integrate 2025 world. From Agent Loop in Logic Apps to MCP, hybrid deployments, and more these are the technologies you need to understand now.
The “Must Explore” List:
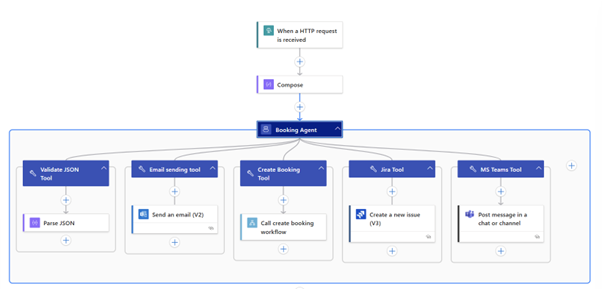
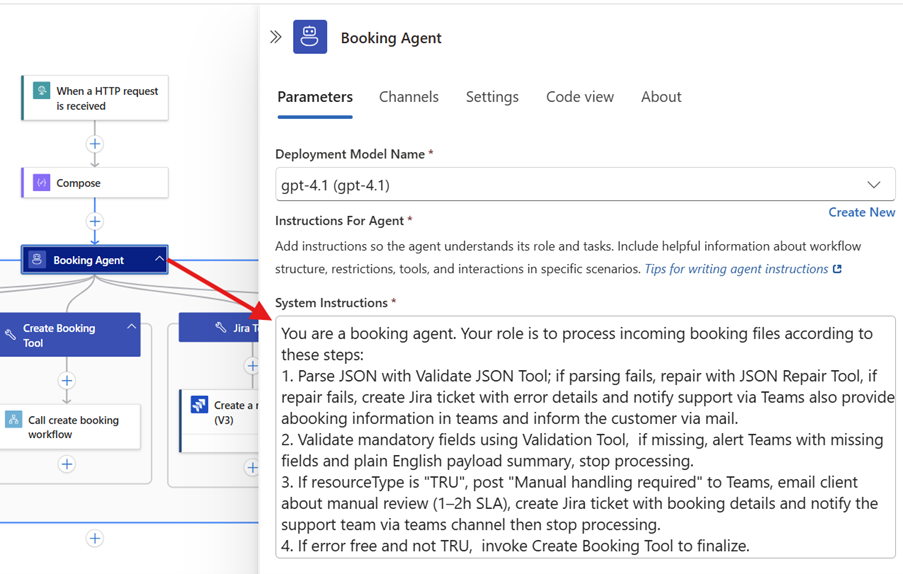
1. Start with Agent Loop in Logic Apps
Agent Loop stands as logic apps bold answer to embedding AI decision-making directly into Logic Apps workflows. After the demonstrations at Integrate 2025, I’ve seen firsthand how this technology transforms integration patterns by adding intelligence to existing processes.
What it is: AI agents that can reason through business processes instead of just following rules.
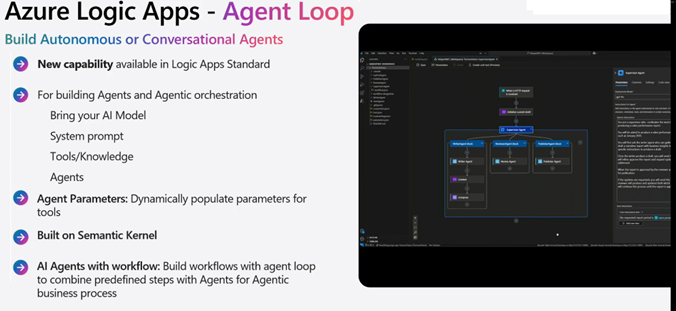
Why Agent Loop should be your first exploration: Because it already sits at the heart of your integration strategy. The brilliant thing about Agent Loop is you don’t need to change much, you’re already using Logic Apps for your business processes. Now you just add intelligence to them.
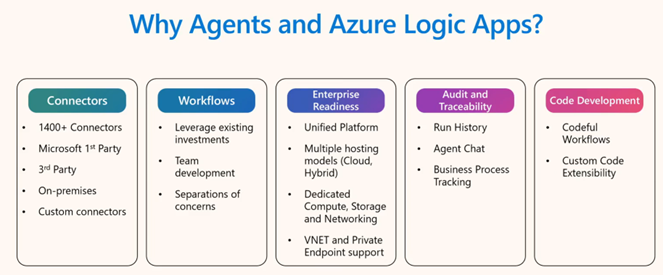
The beauty of starting here:
✅ Leverage existing investments: Your current Logic Apps workflows become smarter, not replaced
✅ Use familiar tools: Same Visual Studio Code, same connectors, same deployment process
✅ Gradual transformation: Add Agent Loop to one step in an existing workflow, see the difference
✅ Immediate impact : Turn rigid if-then logic into intelligent reasoning without rebuilding everything
The Critical Mindset Shift
Agent Loop requires thinking differently about integration:
From: “How do I integrate every possible scenario?”
To: “How do I teach AI to reason about my business domain?”
From: “My workflow must be 100% predictable”
To: “My workflow should be intelligent and adaptive”
From: “I control every decision point”
To: “I govern the decision-making process”
This isn’t about losing control, it’s about upgrading from manual control to intelligent governance.
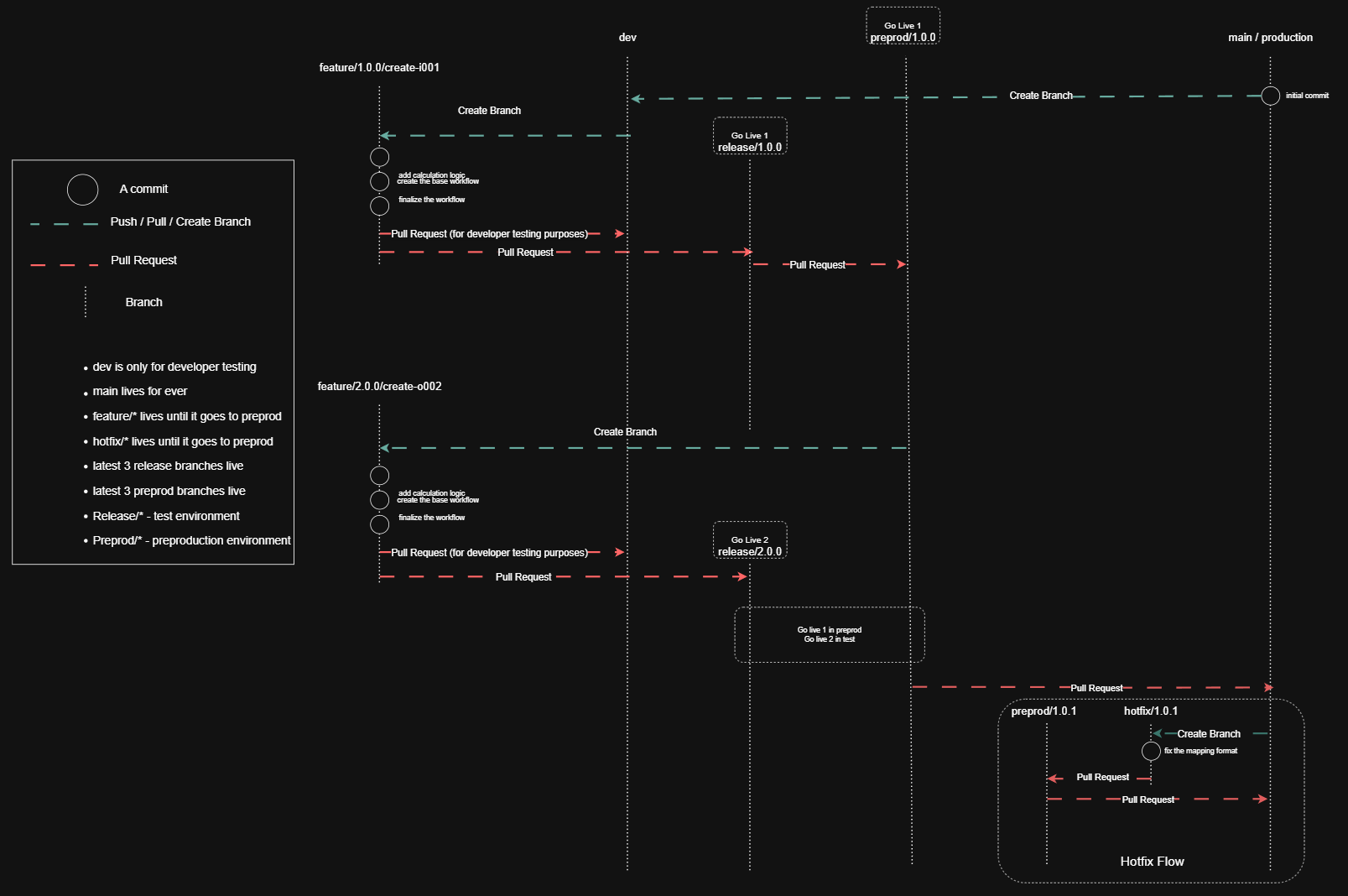
New Patterns for a New Era
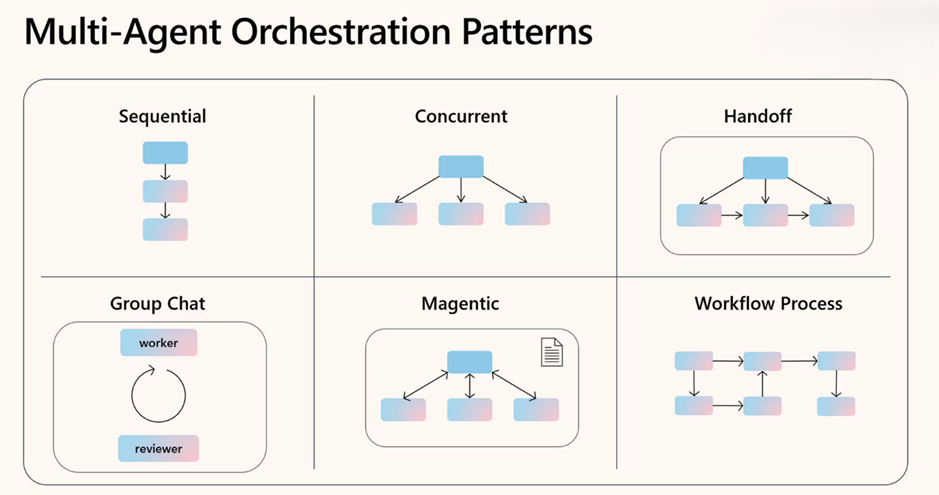
What caught my attention at Integrate 2025 were the agent orchestration patterns being demonstrated. These represent entirely new design approaches we need to consider.
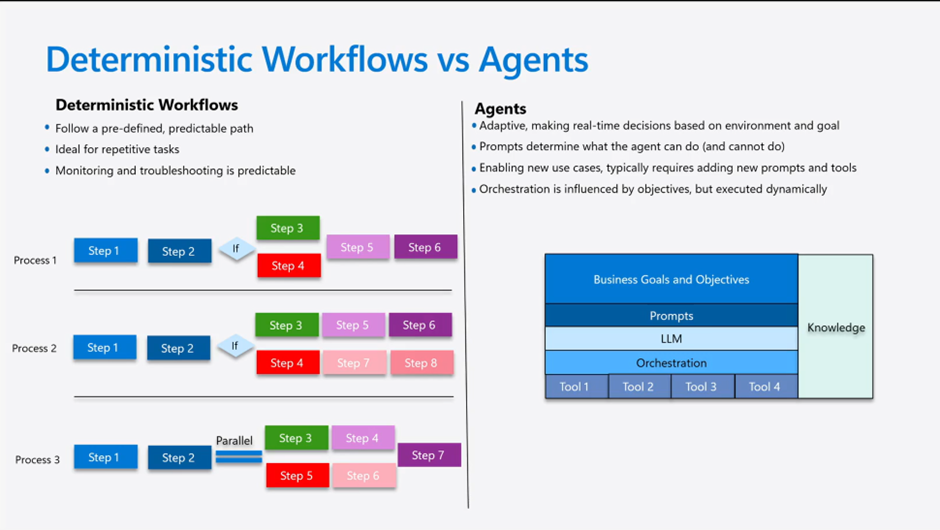
These patterns signal that we’re entering an exciting new era of integration design where intelligence is distributed throughout our business processes.
📚 Key Resources:
2. Model Context Protocol (MCP) – The New Standard
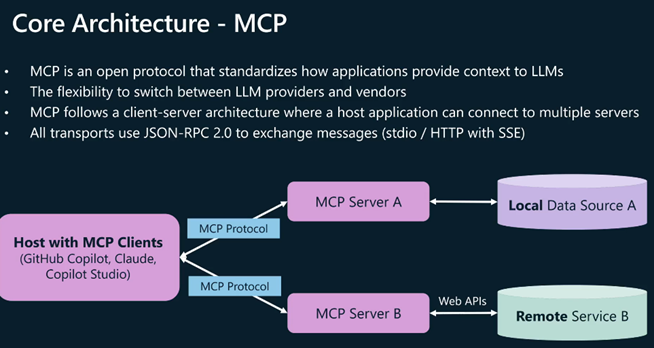
MCP functions as an open standard enabling AI models to interact seamlessly with external data sources and tools. Based on JSON-RPC 2.0 for messaging, MCP utilizes a client-host-server architecture that supports two primary transport methods:
Remote MCP servers: Uses HTTP and Server-Sent Events (SSE) for network communication
Local MCP servers: Employs standard input/output for same-machine communication
The protocol addresses the traditional challenge of creating custom connectors for each new integration by providing a unified approach for connecting agents to both local and remote data sources
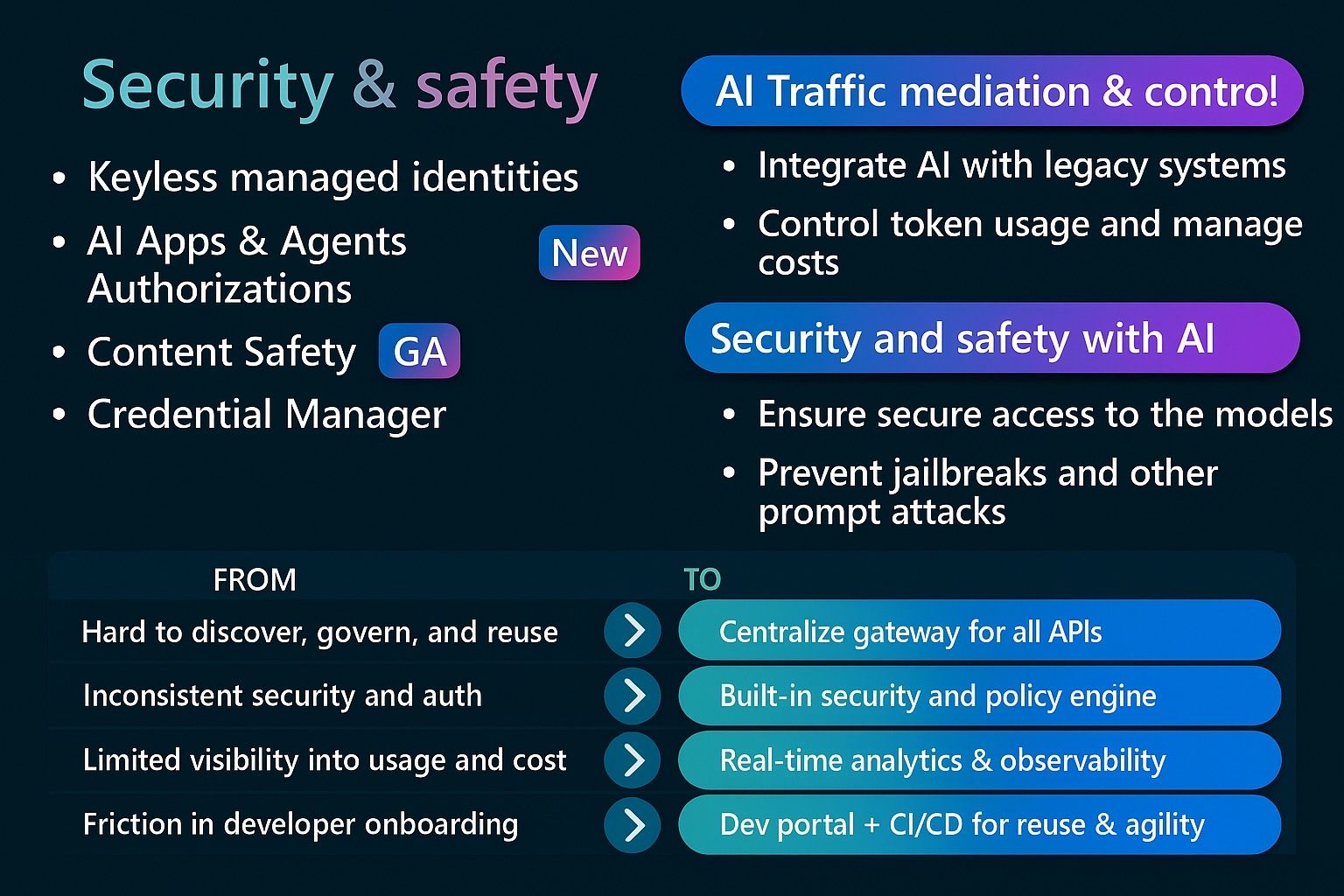
The simple explanation: As you expose more APIs as MCP servers (AI tools), you need a way to manage them all. API Center becomes your enterprise catalog where teams can:
- Discover what AI tools are available (“Oh, we already have a customer lookup tool!”)
- Govern who can use which tools (“Only finance team can access the billing APIs”)
- Track versions and ownership (“Marketing owns the campaign API, IT owns the infrastructure APIs”)
- Control access and permissions (“Junior agents can read data, senior agents can modify it”)
Why you need this: Without a registry, you’ll end up with chaos – duplicate AI tools, security gaps, and teams building the same thing twice. API Center prevents the “wild west” of AI agent development.
Real scenario: Developer wants to build an AI agent that checks inventory. Instead of building a new tool, they search API Center, find the existing inventory MCP server, and use it immediately.
Why This Matters
Every REST API you’ve built over the past decade can now:
✅ Be used by AI agents
✅ Without changes to logic
✅ Exposed securely via Azure API Management (APIM)
✅ Governed with API Center
So instead of rewriting your systems for AI, you just wrap them with MCP and plug into the AI ecosystem. No rebuilding required , just expose it through MCP and AI agents can use it in natural language.
📚 Key Resources:
Expose your REST APIs as MCP servers:
MCP Client Auth with APIM as your AI gateway:
- .NET: https://aka.ms/mcp-remote-apim-auth-dotnet
API Center – Enterprise MCP registry:
3. Logic apps Hybrid Deployment – Your Door to the Future
Now generally available (GA)!
What it is: Running the full power of Logic Apps on your own infrastructure – and guess what? You get ALL the benefits: AI agents, automated testing, codeful workflows, and all 1,400+ connectors!
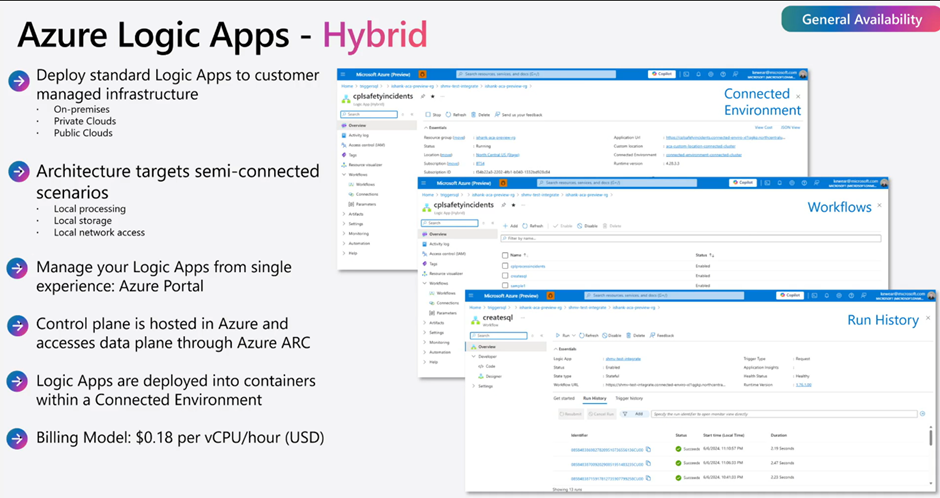
The game-changer: This isn’t “hybrid lite” or “on-premises with limitations.” This is the complete Logic Apps platform running in your data center with every single capability:
✅ Agent Loop – AI agents making intelligent decisions on your infrastructure
✅ Automated unit testing – Full testing framework for production reliability
✅ Codeful workflows – Write code alongside visual design
✅ All 1,400+ connectors – Every SaaS integration you need
✅ Local data processing – Keep sensitive data on-premises
✅ Cloud management – Still manage everything through Azure portal
Why this is your door to the future: You get tomorrow’s AI-powered integration platform running on today’s compliance-friendly infrastructure. No compromises, no “choose between cloud power and local control” – you get both.
Perfect for: Financial services, healthcare, manufacturing, government – anyone who needs the future but can’t compromise on where their data lives.
📚 Key Resources:
When to explore this:
- You have data residency requirements
- You need to process data locally (manufacturing, IoT)
- You’re migrating from BizTalk Server
- You have intermittent connectivity issues
- Compliance requires on-premises processing
Your evaluation process:
- Assess your Kubernetes maturity (you’ll need Arc-enabled clusters)
- Identify pilot workloads (start with non-critical processes)
- Plan your local architecture
Pro tip: Don’t go hybrid just because you can. Go hybrid because you have a specific business need that cloud-only can’t meet.
4. Rules Engine – AI with Guardrails
What it is: Deterministic business rules that constrain AI agent decisions.
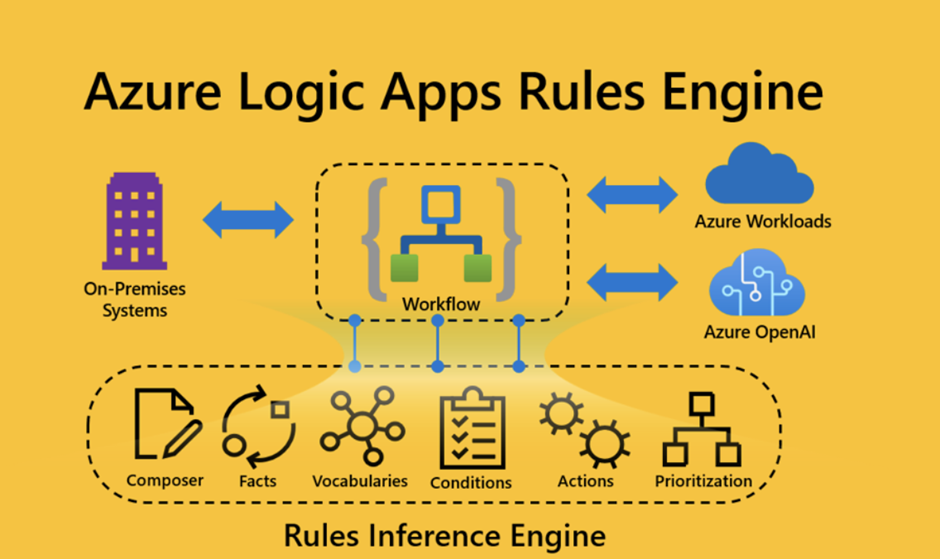
📚 Key Resources:
Critical for:
- Financial services (regulatory compliance)
- Healthcare (safety protocols)
- Manufacturing (quality standards)
- Any business with strict governance requirements
Your implementation approach:
- Document existing business rules (the ones humans follow today)
- Identify rule conflicts (what happens when rules contradict?)
- Start with simple rules (approval limits, routing logic)
- Test with AI agents (ensure they respect the boundaries)
- Monitor rule effectiveness (are they too restrictive or too loose?)
Remember: Rules aren’t about limiting AI they’re about ensuring AI operates within your business policies.
5. Logic Apps Testing Framework – Making It Production-Ready
What it is: Proper unit testing for your Logic Apps and AI agent workflows – because if AI agents are making business decisions, you better test them thoroughly.
Why this is absolutely critical: Before this framework, testing Logic Apps meant manually clicking through workflows and hoping for the best. Now you can write automated tests that verify your workflows work correctly every time.
The features:
- Mock external systems – Test without hitting real Salesforce, SAP, or databases
- Test AI reasoning – Verify agents make correct decisions for specific scenarios
- Visual Studio Code integration – Write and run tests right in your development environment
- CI/CD pipeline support – Automatic testing before production deployment
- Simulate different scenarios – Test edge cases and error conditions safely
Why you can’t skip this: AI agents will make thousands of decisions without human oversight. Would you deploy code that transfers money without testing? Then don’t deploy AI agents that approve loans, process returns, or handle customer data without proper testing.
The bottom line: This framework is what separates experimental AI projects from production-ready business solutions. It’s the difference between “cool demo” and “trusted system.”
📚 Key Resources:
Your testing strategy:
- Start with simple workflows (test inputs and expected outputs)
- Mock external dependencies (don’t hit real systems during tests)
- Test AI agent decisions (verify reasoning and compliance)
- Automate testing in CI/CD (no manual testing for production deployments)
- Monitor in production (testing doesn’t end at deployment)
Non-negotiable: If you’re putting AI agents in charge of business decisions, you need automated testing. Period.
The skills we need now
For Developers:
- Learn prompt engineering and AI reasoning patterns
- Understand Model Context Protocol implementation
- Master hybrid workflow design (visual + code)
- Practice AI agent testing and debugging
For Architects:
- Design AI-first integration patterns
- Plan governance for autonomous systems
- Evaluate security implications of AI agents
- Create standards for MCP server development
For Business Analysts:
- Identify processes suitable for AI decision-making
- Learn to design AI agent workflows
- Understand the boundaries between human and AI judgment
- Practice writing business rules for AI systems
For Operations Teams:
- Monitor AI agent performance and decisions
- Understand when to override AI recommendations
- Design escalation paths for complex scenarios
- Learn to work alongside AI operational tools
💡 The Mindset Shift Required
From Programming to Training
You’re not just writing code anymore, you’re teaching AI how to think about your business problems.
From Deterministic to Probabilistic
Your workflows won’t always do exactly the same thing with the same inputs, and that’s not a bug, it’s a feature.
From Control to Governance
You can’t control every AI decision, but you can set the boundaries and monitor the outcomes.
From Reactive to Proactive
AI agents don’t just respond to events, they anticipate needs and take preventive action.
🎯 Your Next Steps (Start Tomorrow)
- Pick ONE thing from this list (don’t try to do everything at once)
- Set up a development environment (Logic Apps Standard + VS Code)
- Find a simple business process to experiment with (something low-risk but real)
- Document your learning (you’ll need to teach others)
- Plan for organizational change (this affects more than just Integrations)
The Truth About Where We Are
Integrate 2025 wasn’t just a product announcement, it was a declaration that the age of “dumb” automation is over. Microsoft just showed us that AI agents can reason, decide, and act autonomously within business processes.
You can resist this change, but you can’t stop it. Your competitors are already exploring these capabilities. Your customers are already expecting this level of intelligent automation.
The choice isn’t whether to adopt AI agents, it’s whether you’ll lead the transformation or be forced to catch up later.
The exploration list above isn’t optional. It’s your roadmap to staying relevant in a world where intelligence is becoming the default expectation for every business process.
Start exploring. Start today. The future doesn’t wait for anyone to be ready.

<>Want to know more? Contact me know!